10+ cdn network diagram
Featuring our two most popular panels - Super Two and Turbo Superterm. Azure is Microsofts public cloud computing platform that provides cloud services for analytics storage and networking.

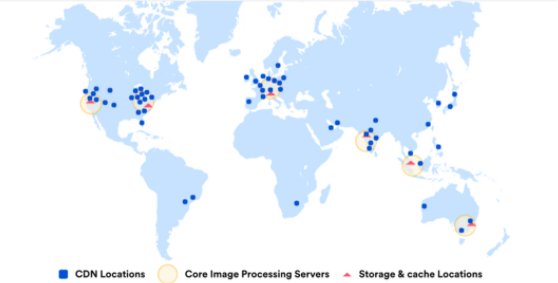
Our Anycast Network Map Cloudflare Map Content Delivery Network Cloud Services
Custom policies are configuration files that define the behavior of your Azure Active Directory B2C Azure AD B2C tenant.

. The following table shows response times that you can expect for all users running a test against a sample configuration in a query. Cloud Storage sets the Content-Type. Updates can be flighted to test devices prior to broader distribution.
The social network perspective provides a set of methods for analyzing the structure of whole social entities as well as a variety of theories explaining the patterns observed in these structures. With you every step of your journey. BitTorrent is a communication protocol for peer-to-peer file sharing P2P which enables users to distribute data and electronic files over the Internet in a decentralized manner.
A simulation is the imitation of the operation of a real-world process or system over time. 15 Block Diagram 5 2 Pin Definitions 6 21 Pin Layout 6 22 Pin Description 6 23 Power Scheme 8 24 Strapping Pins 9 3 Functional Description 10 31 CPU and Memory 10 311 CPU 10 312 Internal Memory 10 313 External Flash and SRAM 10 314 Memory Map 11 32 Timers and Watchdogs 13 321 64-bit Timers 13 322 Watchdog Timers 13 33 System. Include them anyway you likeSVGs SVG sprite or web fonts.
The following workflow diagram describes how the CDN uses token authentication to work with your web app. The model represents the key characteristics or behaviors of the selected system or process whereas the simulation represents the evolution of the model over timeOften computers are used to execute the simulation. Built on Forem the open source software that powers DEV and other inclusive communities.
Integrate your apps through APIs messaging and networking tools A toolkit to rapidly create secure and manage APIs Codeless connectors for your data apps and APIs UI and CLI to rapidly move large files Virtualization for x86 AIX System i and Power applications PaaS stream processing based on Apache Kafka Tools to connect all of your apps data and events PaaS. Free high quality open source icon library with over 1600 icons. Updates can be applied to the operating system and device drivers as well as OEM-specific applications and files.
While user flows are predefined in the Azure AD B2C portal for the most common identity tasks custom policies can be fully edited by an identity developer to complete many different tasks. Patents may cover the specifications techniques or network interfacesystem characteristics disclosed herein. This is illustrated by the following diagram.
Setting up token authentication. The time a test takes is based on the size of your VPC network configuration and the number of Google Cloud resources that you use. The clusters VPC network must be configured to use a 1500 byte MTU.
The computers are geographically close together that is in the same building. In this article. Cloud CDN inspects the Content-Type HTTP response header which reflects the MIME type of the content being served.
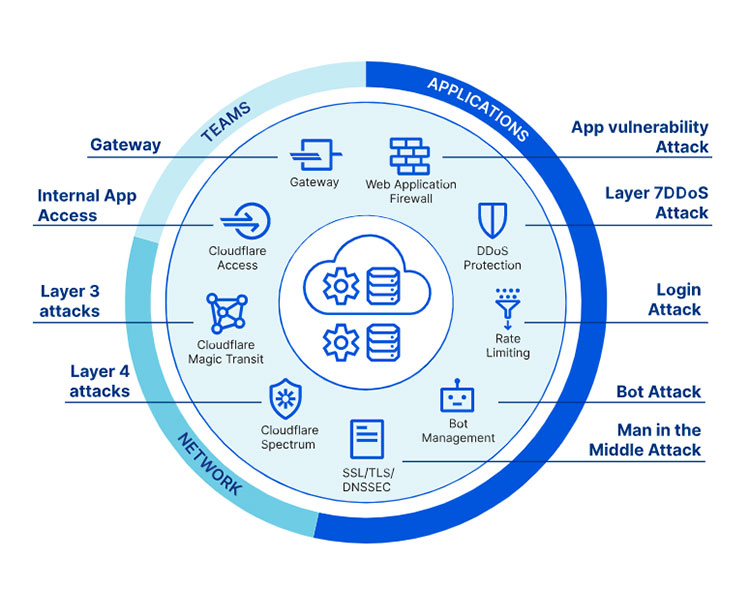
These updates are distributed by the same content distribution network CDN as Windows Update which is used daily by millions of Windows customers around the world. The on-edge position also makes a CDN ideal for blocking DDoS floods which need to be mitigated outside of your core network infrastructure. Choose from six Continental CardAccess 3000 Paks including choice of either HID or Xceed readers cards plus Continental Controller and new CardAccess 3000-5 version 25 improved enterprise class scalable access control kits and packages with support for 1 host 4.
With you every step of your journey. Getting Connectivity Tests results can take from 30 seconds to up to 10 minutes. This Amazon Web Services architecture diagram depicts a VPC containing business solutions on AWS.
Clusters use the MTU of the underlying VPC network which is normally 1460 bytes. Simulations require the use of models. Token validation logic on CDN endpoint.
Free CDN option for all sites. M3 10 of NU DPP Cycle 2 Phase 1 M2 See Note 2 M4 20 of NU M3 M2 See Note 2 Notes. In computing a denial-of-service attack DoS attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a networkDenial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an.
The diagram below illustrates where we intend to place graduates of the Industrial Network Cybersecurity program. As we can see the system made in the Microsoft Azure network may range from simple to complex. There are many types of computer networks including the following.
Ultrafast PHP available for up to 30 faster sites. A network is defined as a group of two or more computer systems linked together. 1 Effective September 19 th 2018 for new cycles Affected System Stability and Short Circuit Studies are required only for DPP Phase 2 and DPP Phase 3 2 M3 and M4 will be adjusted based on previously paid M3 and M4 for Provisional Requests.
The computers are farther apart and are connected by telephone lines or. To make use of a 1500 MTU network all of the following must be true. Your origins web server software must set the Content-Type for each response.
9-1-1 SSP representative to ensure compatibility with the 9-1-1 network and their legal counsel to ensure compliance with current regulations. Many web servers automatically set the Content-Type header including NGINX Varnish and Apache. Dreftymac TempEngWeb016 CC BY-SA 30 This approach allows you to reuse static web page elements while defining dynamic elements based on.
There are two ways to make an AWS. No license is granted whether expressed or implied. The following flowchart describes how Azure CDN validates a client request when token authentication is configured on CDN endpoint.
Intra-node-visibility must be enabled for the cluster and. Roger Gale Faculty Computer Information Systems and David Leversage Faculty Electrical and Computer Engineering talk about the launch of the Industrial Network Cybersecurity program the first of its kind in Canada. This document shall not.
The cluster version must be GKE 115 or higher and. BitTorrent clients are available for. NGINX direct delivery of static resources dynamic cache switched on for all by default Memcache option.
A custom policy is fully configurable. Integrate your apps through APIs messaging and networking tools A toolkit to rapidly create secure and manage APIs Codeless connectors for your data apps and APIs UI and CLI to rapidly move large files Virtualization for x86 AIX System i and Power applications PaaS stream processing based on Apache Kafka Tools to connect all of your apps data and events PaaS. DEV Community A constructive and inclusive social network for software developers.
A social network is a social structure made up of a set of social actors such as individuals or organizations sets of dyadic ties and other social interactions between actors. Load Balancing Load balancing is all about having a traffic guard positioned in front of your servers alternating the flow of incoming requests in such a way that traffic jams are avoided. Users may operate a variety of applications for low cost including computation memory machine analysis big data CDN databases IoT Internet of Things privacy and apps.
It supports virtual machines web apps mobile apps virtual networking DNS CDN etc. Google cloud with SSD-persistent storage and ultra-fast network. It is important to create a visual representation of systems using standard.
To send or receive files users use a BitTorrent client on their Internet-connected computerA BitTorrent client is a computer program that implements the BitTorrent protocol.

2 5 Years Later The Network Diagram R Homelab
2
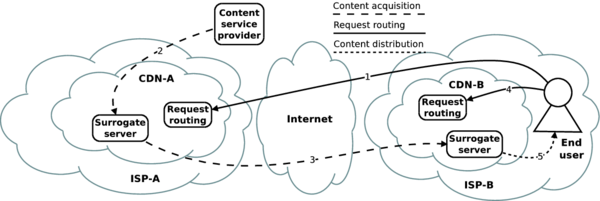
Content Delivery Network Interconnection Wikiwand
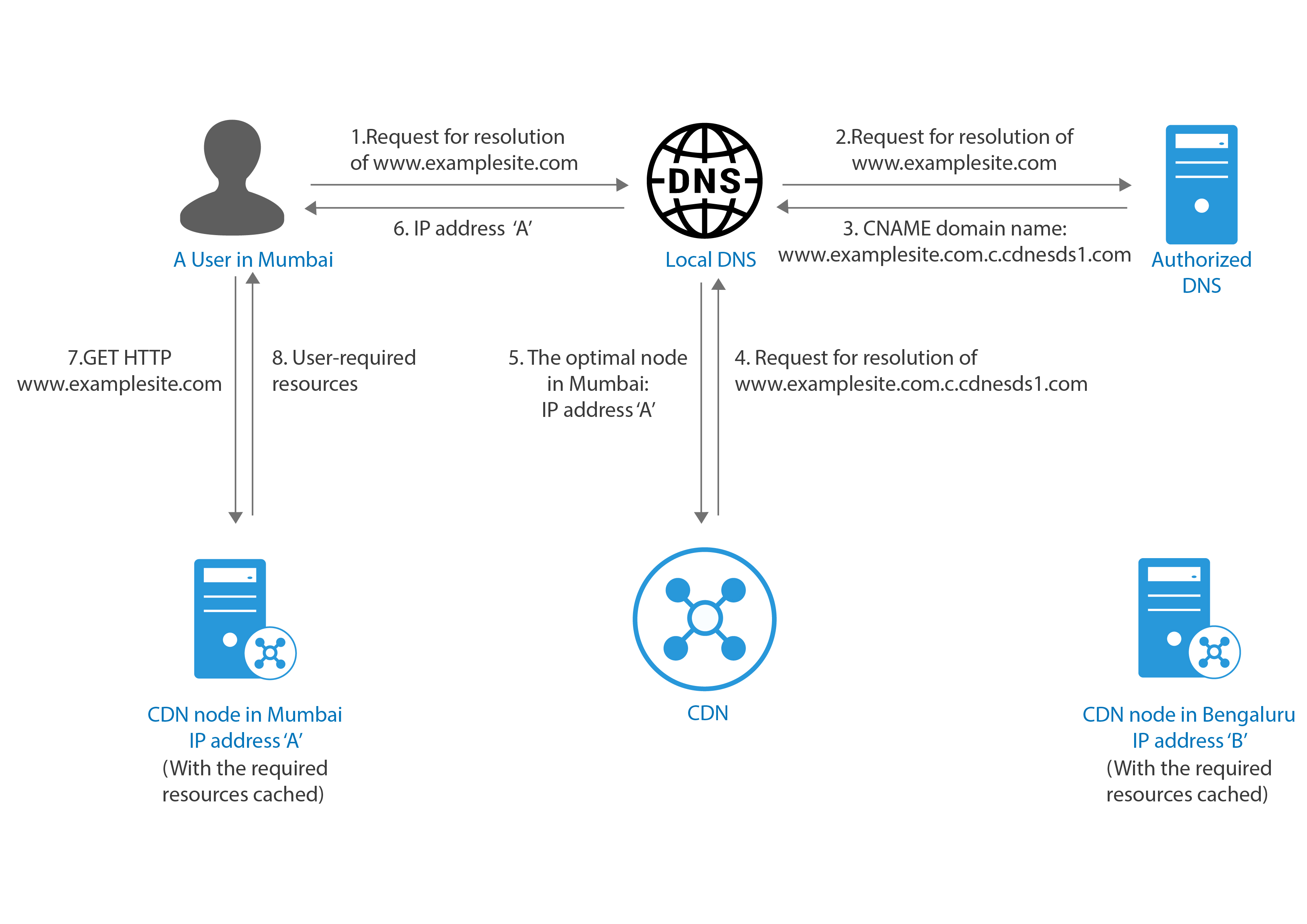
What Are The Advantages And Disadvantages Of Adding Javascript Libraries Jquery For Example By Linking Them To A Remote Content Delivery Network Cdn As Compared To Having A Local Asset Linked
What Is A Cdn Knowledge Base Scalahosting

2 5 Years Later The Network Diagram R Homelab

2 5 Years Later The Network Diagram R Homelab
Y6i9k2gevkrhzm

We Build Your Private Cdn
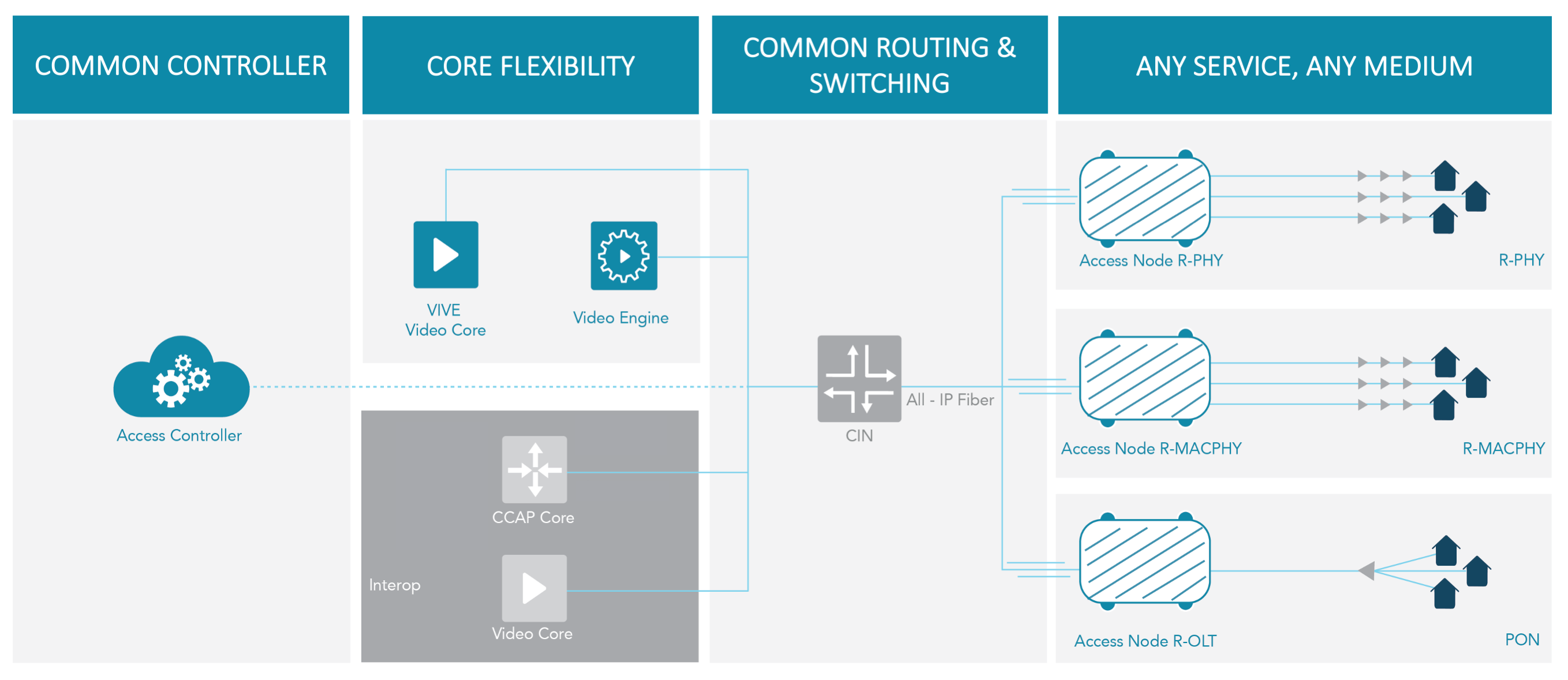
Network Access Vecima Networks Inc
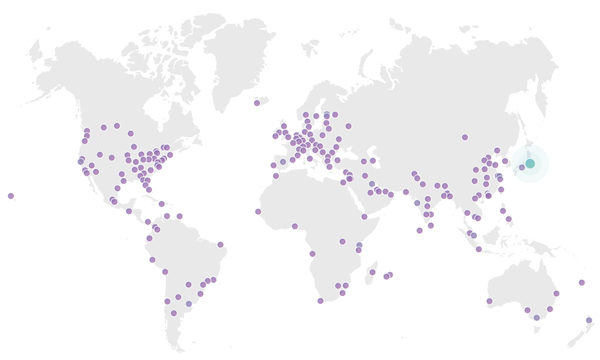
The All New Cdn Finder Cdn Planet
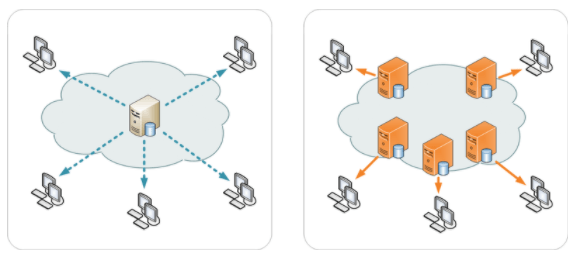
What Is A Cdn Knowledge Base Scalahosting
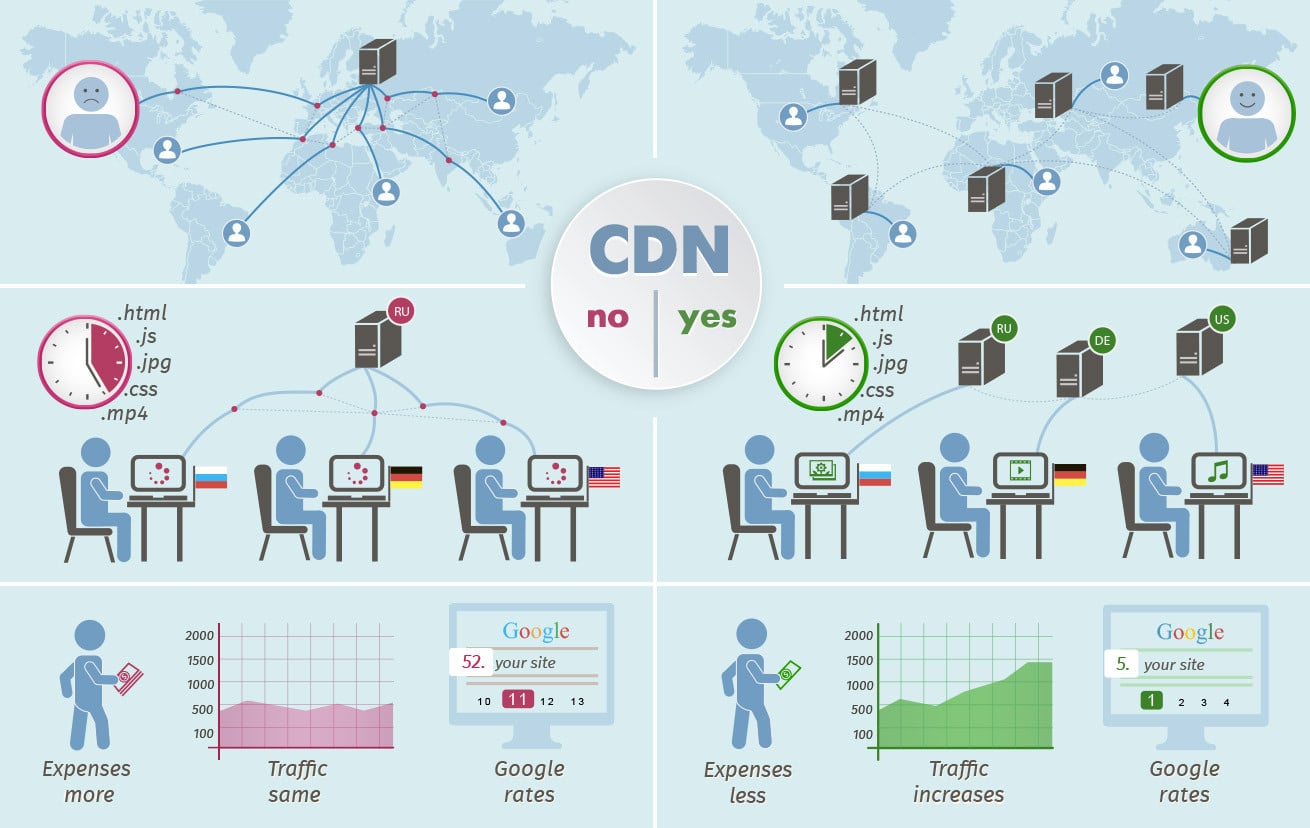
10 Content Distribution Tactics To Maximize Exposure In 2019
:filters:format(jpeg)/f/51376/1060x600/ed0e6e7bbc/cloudfront-network-map-10jan2020-b1688f3667389422c5abbc6de171ba98e32a2168.png)
Content And Asset Cdn Storyblok

Content Delivery Network Wikiwand

2 5 Years Later The Network Diagram R Homelab

2 5 Years Later The Network Diagram R Homelab